Introduction
Healthcare breaches keep rising, and fines now reach over $2 million annually. In 2025, HHS audits are stricter and far more frequent.
Passing means proving complete control over PHI (aka the patient data), from access logs to staff training, with no gaps in your HIPAA compliance requirements checklist.
This guide gives you a clear HIPAA compliance checklist updated for 2025 rules, with role-based steps and a free HIPAA compliance checklist PDF.
Download the HIPAA Compliance Checklist available in this guide to start mapping owners, timelines, and evidence today. Built with input from auditors and CISOs
Let us show you exactly how to implement the safeguards and prepare documentation that makes your HIPAA audit straightforward.
Quick Summary
You need a quick overview before diving into the details. Here are the most important HIPAA compliance changes and requirements for 2025.
- All HIPAA Security Rule specifications shifted from “addressable” to mandatory, meaning no optional safeguards remain.
- Multi-factor authentication and encryption of ePHI at rest and in transit are now required controls.
- Breach notifications must occur within 24 hours for certain high-severity security incidents.
- Covered entities and business associates face annual internal audits and stricter documentation rules.
- Maximum annual civil penalties now exceed $2 million, while criminal penalties remain up to 10 years imprisonment.
- Compliance applies to healthcare providers, health plans, business associates, and subcontractors handling patient data.
- The fastest way to pass audits is to use a HIPAA compliance software checklist that assigns owners, tracks evidence, and prevents gaps.
Start with ComplyJet’s HIPAA compliance software checklist, which maps tasks to responsible owners, sets due dates, and stores the evidence needed to pass your HIPAA compliance audit checklist.
Let's start with the foundation.
What is HIPAA Compliance in 2025?
HIPAA compliance in 2025 means meeting the Health Insurance Portability and Accountability Act requirements to secure protected health information and maintain patient trust.
The law’s goals are clear: protect medical records, prevent unauthorized access, and ensure electronic protected health information stays safe across all systems.
Five rules define compliance: Privacy Rule, Security Rule, Breach Notification Rule, Enforcement Rule, and Administrative or Omnibus Rule for business associates.
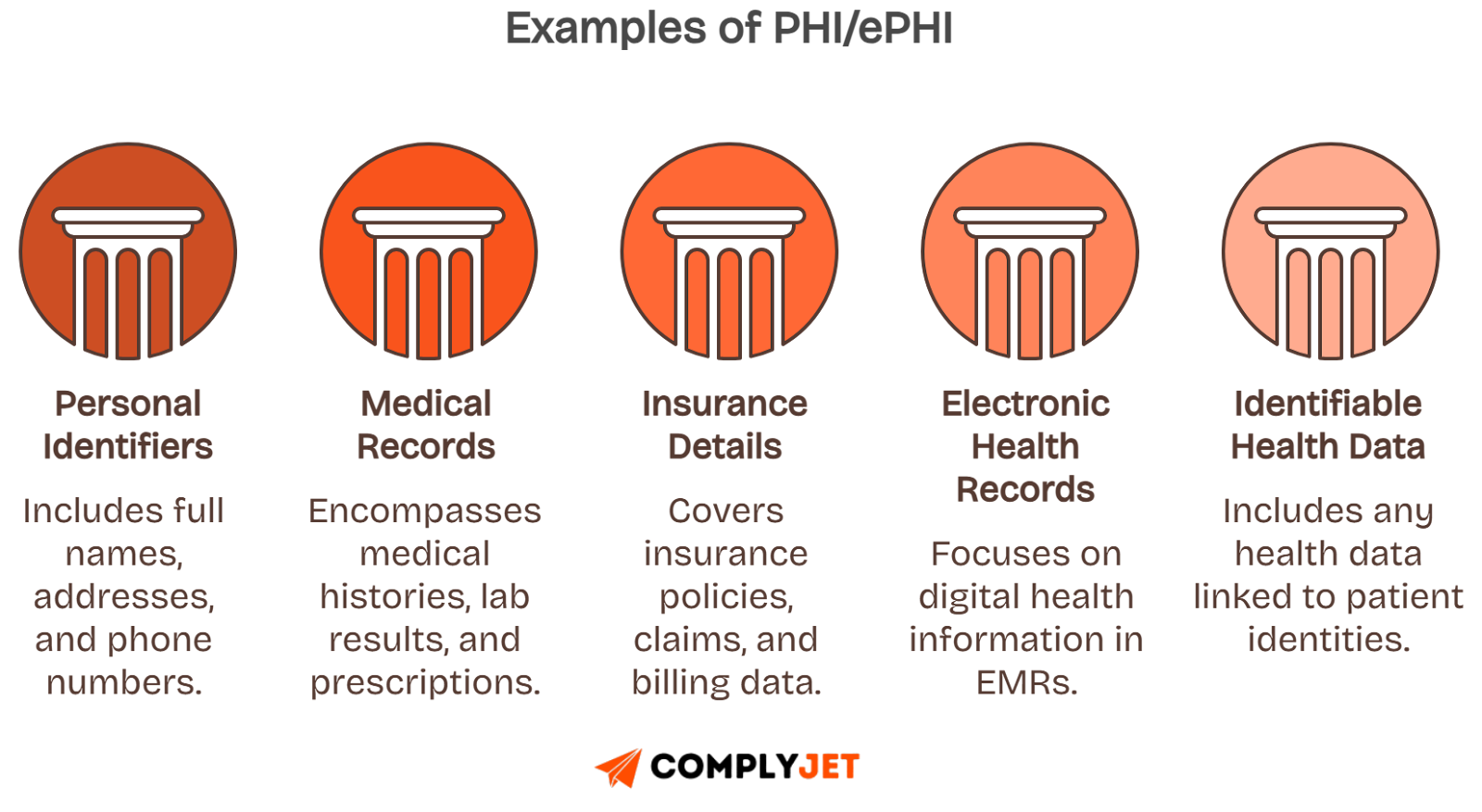
Protected health information includes names, contact details, medical histories, or insurance identifiers. Even partial data tied to medical records can trigger HIPAA scope.
See: HIPAA Business Associate Agreement (BAA) for required contractual safeguards when sharing PHI with external vendors.
Once you understand HIPAA rules and PHI scope, the next step is knowing exactly who must comply with these requirements.
Who Must Comply? (Covered Entities & Business Associates)
HIPAA compliance applies to covered entities and business associates who access or manage protected health information in any form.
Covered entities include healthcare providers such as hospitals, clinics, doctors, dentists, pharmacies, and any group using electronic medical records.
Health plans like insurance carriers, HMOs, employer health benefits, and government programs must also follow HIPAA compliance requirements.
Business associates include IT vendors, billing companies, cloud storage providers, law firms, and subcontractors who handle electronic protected health information.
Simple Checklist To Determine If you Must Comply
Healthcare providers, dental offices, telehealth services, and software vendors each have compliance nuances that depend on how they manage patient data.
Seamless transition: With compliance roles clarified, let’s look at what changed in 2025 and why the Security Rule is now stricter.
What Changed in 2025 and Why It Matters?
HIPAA compliance in 2025 tightened with enhanced Security Rule requirements, faster breach notifications, and more frequent audits by regulators.
All addressable safeguards are now required, making multi-factor authentication, encryption, and access controls mandatory across electronic protected health information systems.
Organizations must maintain annual asset inventories, conduct internal audits, and document incident response to reduce risks of security incidents or unauthorized access.
These changes mean your HIPAA Security Rule compliance checklist must be updated to reflect mandatory safeguards, reduced reporting timeframes, and stronger technical controls.
Now that you know what changed, the next step is following a complete HIPAA compliance checklist to implement safeguards effectively.
The Complete Step-by-Step HIPAA Compliance Checklist
Think of HIPAA compliance like building a house. Each layer adds protection. If you skip one, the entire structure weakens. Below are the ten steps you must follow, who should own them, the evidence to keep, and how automation tools like ComplyJet can make it easier.
1) Determine Applicability & Scope
Start by figuring out if you are a Covered Entity (CE) or a Business Associate (BA). Covered Entities are hospitals, clinics, pharmacies, and health plans. Business Associates are vendors or contractors who handle PHI (like billing firms, IT providers, or cloud storage vendors).
Now, make an inventory of every system that touches protected health information. This includes EMRs, integrations, email servers, backup storage, and even cloud tools where patient data is stored or transmitted.
Finally, map your data flows. Show how PHI moves across apps, vendors, and integrations. This helps you identify weak spots where data could leak.
Evidence you must keep:
- Full list of systems holding PHI
- Data flow diagrams
- Vendor registers with services noted
ComplyJet advantage: automatically discovers assets, catalogs vendors, and creates a ready-to-use HIPAA risk register.
Once you know your scope, the next step is appointing clear roles to manage it.
2) Appoint Roles & Governance
You cannot run HIPAA compliance without clear accountability. Appoint a Privacy Officer to handle policies, training, and patient rights, and a Security Officer to manage safeguards, technical controls, and incident response.
Set up a cross-functional compliance team with representatives from IT, HR, operations, and legal. This ensures every department shares the responsibility.
Document duties and escalation paths. Use a RACI chart (Responsible, Accountable, Consulted, Informed) to make ownership clear when issues arise.
Evidence you must keep:
- Role descriptions and responsibilities
- RACI matrix
- Compliance meeting notes
ComplyJet advantage: assign HIPAA roles, automate reminders, and track accountability across the team.
Once governance is in place, you need to understand and manage risks.
3) Risk Analysis & Risk Management
A risk assessment identifies risks (for example, weak encryption or missing MFA). A risk analysis goes deeper, rating the likelihood and impact of those risks. Auditors want to see both.
List threats to confidentiality (unauthorized access), integrity (data changes), and availability (system outages). Rate how likely each is and what damage it could cause.
Build risk treatment plans with timelines. Some risks may need fixes (patches, training), while others may be accepted with documentation.
Evidence you must keep:
- Risk register
- Likelihood/impact scoring
- Risk treatment plan with deadlines
ComplyJet advantage: guided workflows for assessments, automated scoring, and exports formatted for audits.
Once risks are managed, the next step is enforcing safeguards, starting with administration.
4) Administrative Safeguards
Administrative safeguards are the rules and processes that shape compliance. Write policies for risk management, sanctions, and security procedures, and update them often.
Control workforce security. Grant the least amount of access needed, ensure new hires are properly onboarded, and remove access quickly when staff leave.
Deliver training to every employee when hired, once a year, and whenever policies change. Keep signed attestations and training logs for six years.
Evidence you must keep:
- Policies and procedures
- Training logs with attestations
- Sanction logs for violations
ComplyJet advantage: prebuilt policy library, training LMS, and attestations tracking with version control.
With policies covered, you must secure the physical environment where PHI lives.
5) Physical Safeguards
Physical safeguards prevent unauthorized access to spaces and devices that handle PHI. Control facility access with locks, keycards, visitor logs, and security cameras.
Secure workstations by placing screens away from public view, using locks, and enabling automatic timeouts.
Track devices and media like laptops, USBs, and external drives. Encrypt them, and securely wipe or shred when they’re no longer used.
Evidence you must keep:
- Visitor logs
- Device inventories
- Secure disposal certificates
ComplyJet advantage: track physical assets and attach compliance evidence to each.
With physical controls in place, you move into technical safeguards.
6) Technical Safeguards
Technical safeguards protect data inside systems. Use unique user IDs, enforce MFA, and enable automatic logoff. Document how emergency access is handled.
Enable audit controls. Collect logs with key details: user ID, action, record accessed, date, and success or failure. Review these logs regularly.
Protect data integrity and transmission security. Use hashing to detect tampering, TLS 1.2+ for communication, and AES-256 for stored data.
Evidence you must keep:
- Access logs
- Audit trail reports
- Encryption configuration reports
ComplyJet advantage: integrates with SIEM, MDM, EDR, and IAM tools, pulling evidence automatically.
With systems secured, you must also hold vendors accountable.
7) Business Associates & BAAs
Every vendor that touches PHI must sign a Business Associate Agreement (BAA). This includes IT providers, cloud vendors, billing companies, and even subcontractors.
BAAs must include clauses for permitted uses, required safeguards, breach notification, contract termination, and subcontractor flow-downs.
Monitor vendors by requesting SOC 2 or ISO 27001 reports, pen-test results, or compliance questionnaires each year.
Evidence you must keep:
- Signed BAAs
- Vendor reports and questionnaires
- Vendor compliance review notes
ComplyJet advantage: vendor due diligence tools, automatic expiry reminders, and secure artifact storage.
Now that vendors are covered, you need to prepare for breach response.
8) Breach Notification & Incident Response
Not every incident is a breach, but all must be logged. A security incident is any attempt to access PHI. A breach is confirmed exposure or disclosure.
Timelines matter. Notify individuals and HHS within 60 days if more than 500 people are affected. Smaller breaches can be reported annually.
Create a runbook: detect, contain, assess, notify, and document. Use prepared templates for notification letters and incident reports.
Evidence you must keep:
- Incident logs
- Breach notification letters
- Root cause reports
ComplyJet advantage: guided incident response workflows and audit-ready evidence exports.
Once breaches are handled, you must enforce patient privacy rights.
9) Privacy Rule in Practice (Patient Rights)
Patients must receive a Notice of Privacy Practices (NPP). Post it on your website and provide it on their first visit.
Respect patient rights: allow them to access PHI within 30 days (or 15 under new proposals), request corrections, or restrict sharing.
Apply the minimum necessary standard daily. Share only what is required, whether in billing, referrals, or operations.
Evidence you must keep:
- Updated NPP copies
- Access request logs
- Amendment or restriction logs
ComplyJet advantage: automate PHI request workflows with SLA tracking.
To close the loop, compliance must be ongoing. IT is not one and done.
10) Ongoing Monitoring & Internal Audits
HIPAA requires continuous oversight. Review access logs and audit reports every quarter. Run vulnerability scans and tabletop disaster recovery exercises.
Update policies and procedures annually. Track evidence freshness and retain all documentation for six years.
Keep a compliance calendar to manage recurring reviews, BAA renewals, and training cycles.
Evidence you must keep:
- Log reviews
- Scan results
- Policy updates with version history
ComplyJet advantage: always-on monitoring with automated alerts and remediation tasks.
By completing these ten steps, you’ll not only meet HIPAA compliance requirements but also build a program that withstands audits and grows with your business.
Role-Specific Mini-Checklists
HIPAA compliance is not one-size-fits-all. Each team has different responsibilities, and your checklist should reflect that. Here’s a detailed breakdown.
HIPAA IT Compliance Checklist - For IT & Security Teams
As the IT or security lead, you’re responsible for protecting the systems that hold electronic protected health information.
You need to enforce strict identity and access management. Every user must have a unique login, and multi-factor authentication should be enabled everywhere.
Don’t overlook basic hygiene. Patch your systems on schedule, segment networks to reduce attack spread, and monitor devices with antivirus or endpoint detection.
Finally, prepare for the worst. Keep backups secure, test disaster recovery processes often, and maintain change control records for all system updates.
HIPAA Security Rule Compliance Checklist
Once your infrastructure is under control, the next challenge is making sure the software itself is built with compliance in mind.
HIPAA compliance checklist for software development & SaaS Vendors
If you’re a SaaS vendor serving healthcare clients, HIPAA compliance must be designed into your software development lifecycle.
Start with secure development practices. Use static and dynamic testing tools (SAST/DAST) to catch vulnerabilities early, and scan dependencies regularly.
Cloud environments bring unique risks. Encrypt all data, rotate keys securely, and isolate tenants if your system is multi-tenant. Keep detailed logs.
When integrating with EMRs or EHRs, always execute a Business Associate Agreement, minimize data you store, and log all API access.
Software HIPAA Checklist
ComplyJet integrates directly with GitHub, Azure, and AWS to capture this evidence automatically.
Software is one piece. On the ground, clinics and dental offices face very different compliance realities.
For Clinics & Dental Offices - HIPAA compliance checklist dental office
In small clinics and dental offices, compliance risks often come from day-to-day operations where patient information is visible or overheard.
Make sure front desk staff position screens away from waiting areas, shred physical forms, and avoid announcing sensitive details aloud.
Protect patient sign-in sheets by limiting visibility, and wipe or encrypt any reused devices before handing them to another employee.
Secure communications. Emails and faxes must follow HIPAA security guidelines, and staff should receive refresher training with signed attestations every year.
Dental Office HIPAA Checklist
Finally, health plans and clearinghouses must manage HIPAA risk at scale, with large data flows and multiple partners.
For Health Plans & Clearinghouses
If you run a health plan or clearinghouse, your main challenge is controlling how patient data is shared and stored across massive systems.
Always sign data-sharing agreements that clearly define PHI protections with every external partner or third-party processor.
Protect your data warehouse with strict access controls, log every access, and apply de-identification where you can to reduce exposure.
Regularly review partner security evidence like SOC 2 or ISO certifications, and update agreements when compliance requirements change.
Health Plan HIPAA Checklist
With every role aligned, you can now build a unified compliance program that prepares you for audits and ongoing HIPAA monitoring.
Evidence You Must Keep and For How Long
Auditors always ask for proof, so you need to know exactly what evidence to store and how long to keep it.
Core Evidence Categories
Keep signed and dated policies, workforce training records, risk assessments, log reviews, incident reports, and executed Business Associate Agreements.
Maintain access reviews showing who had system permissions, when changes were made, and how access was removed during employee exits.
Evidence Examples
Always version control your documents so you can show what was in place at any point.
ComplyJet offers a centralized evidence vault with audit-ready exports, making retention simple and consistent.
Knowing what to keep is one side of compliance, but understanding penalties helps you weigh the risk of getting it wrong.
HIPAA Penalties & Enforcement in 2025
Penalties in 2025 are tougher, with higher fines and stricter enforcement than ever before.
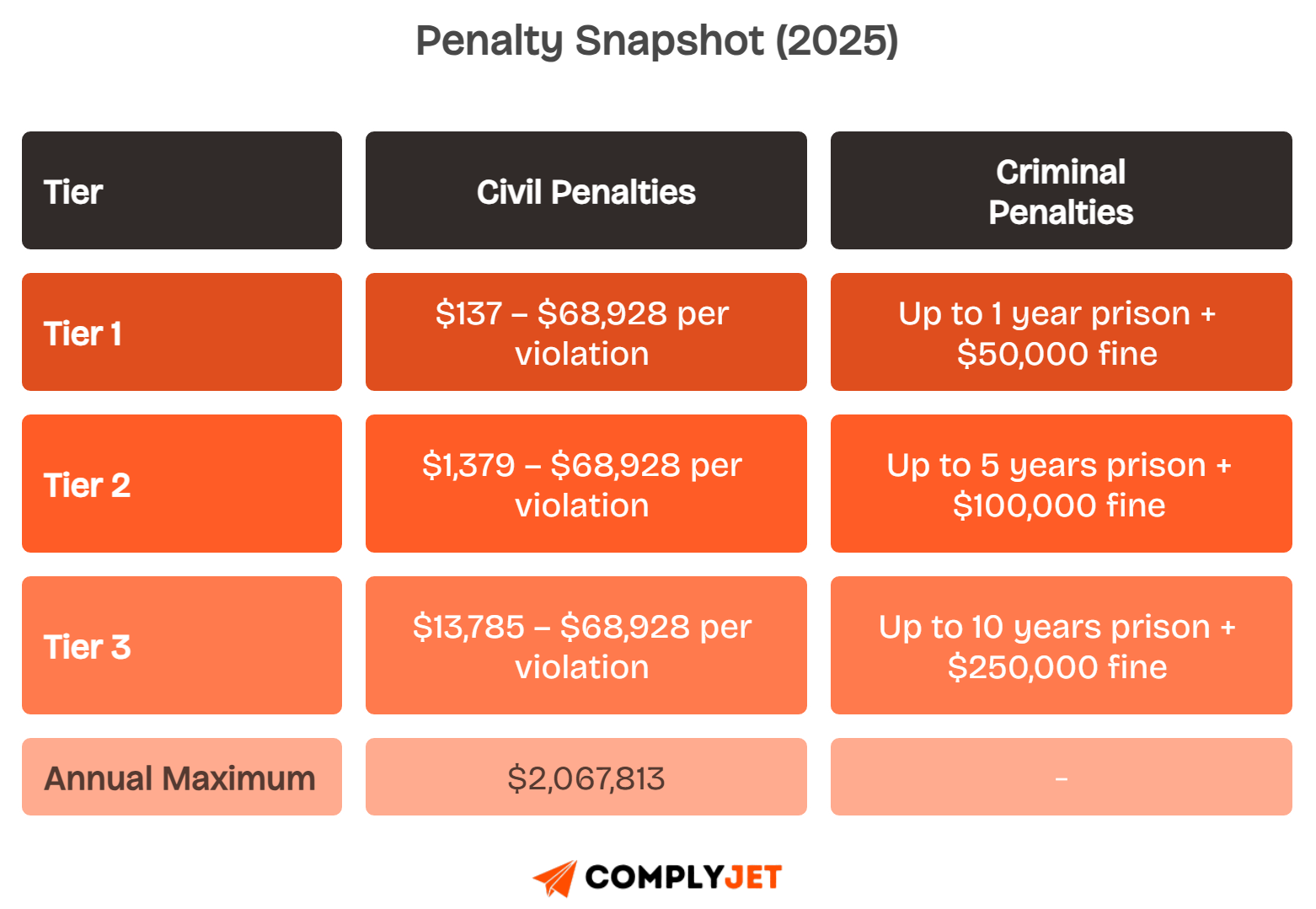
Civil Penalties
Civil penalties scale by tier. Fines range from $137 for minor violations up to $68,928 per violation, capped at $2,067,813 annually.
Each tier depends on whether you acted with knowledge, reasonable cause, or willful neglect, and whether you corrected issues promptly.
Criminal Penalties
Criminal charges apply if violations involve wrongful use or intentional misuse of patient data. Sentences range from 1 to 10 years in prison.
Penalty Ladder
Real-world cases show fines often result from weak access controls, late breach notifications, or missing Business Associate Agreements.
With penalties mapped out, the final step is focusing on prevention strategies that keep you ahead of regulators.
How to Avoid the Most Common HIPAA Violations
Most HIPAA violations happen because organizations miss obvious safeguards. Knowing these mistakes in detail helps you avoid fines and protect patient trust.
Inadequate Risk Analysis
Organizations often treat risk analysis as a one-time project. HIPAA requires ongoing assessments that document threats to confidentiality, integrity, and availability of patient data.
Do this today: Identify all systems that store or transmit PHI, list threats like phishing, lost devices, or misconfigurations, and update the risk analysis yearly.
- Risk Analysis: A process to identify risks and vulnerabilities to PHI.
- Confidentiality, Integrity, Availability (CIA Triad): Core security goals HIPAA enforces.
- PHI: Protected Health Information (any patient data that can identify someone).
Missing MFA and Weak Encryption
Weak logins and unencrypted records make data theft easy. Regulators now expect strong authentication and encryption for all systems with ePHI.
Do this today: Turn on multi-factor authentication for all accounts, encrypt data at rest with AES-256, and encrypt transmissions with TLS 1.2 or higher.
- MFA (Multi-Factor Authentication): Login using two or more factors, like password plus phone code.
- Encryption at Rest: Protecting stored data, even if stolen.
- Encryption in Transit: Protecting data while it moves across networks.
Missing Business Associate Agreements
Vendors often handle PHI without signed BAAs. Without contracts, you’re liable if they cause a data breach.
Do this today: Identify every vendor accessing PHI (cloud, billing, legal, IT), sign a HIPAA-compliant BAA, and renew it before it expires.
- BAA (Business Associate Agreement): A contract required between you and vendors handling PHI.
- Business Associate: A vendor, subcontractor, or partner that uses or processes PHI.
Slow Breach Notifications
Delays in notifying patients or HHS after a breach quickly increase penalties. HIPAA requires prompt disclosure.
Do this today: Create a breach notification plan, use templates for letters, and rehearse your team’s response timeline to ensure compliance.
- Breach Notification Rule: HIPAA rule requiring notifications after PHI breaches.
- HHS (Department of Health and Human Services): Federal agency enforcing HIPAA.
- Security Incident vs Breach: An incident may not expose PHI, but a breach always does.
Poor Physical Controls and Incomplete Logs
Unlocked rooms, visible screens, or missing access logs are easy violations. Physical and technical oversight are as important as digital safeguards.
Do this today: Secure server rooms, position workstations away from public view, enforce automatic screen locks, and maintain access logs for six years.
- Physical Safeguards: HIPAA requirements for securing physical spaces and devices.
- Access Logs: Records showing who accessed PHI and when.
- Retention Period: How long records must be stored (usually 6 years).
Common HIPAA Violations
Once you avoid these violations, your next priority is preparing for the audit itself.
How to Pass the Audit for the First Time
Passing an audit depends on preparation. Auditors want to see proof, structure, and a team that understands its responsibilities.
1) Build a Pre-Audit Packet. Gather all compliance evidence into a single packet with a collection of all documents before an audit. Include policies, org chart, risk analysis, training logs, signed BAAs, and system access records.
Pre-Audit Packet: A collection of documents prepared before an audit.
Policies: Written rules about privacy and security.
Training Logs: Proof staff completed HIPAA training.
2) Prepare Staff for Interviews. Auditors interview key staff. Assign who answers which topic, run mock interviews, and keep answers within scope to avoid over-sharing.
Audit Scope: Boundaries of what auditors can review.
Mock Interviews: Practice sessions that prepare staff for real auditor questions.
Key Roles: Privacy Officer, Security Officer, Compliance Team leads.
3) Maintain secure sharing and redaction. Evidence must be shared securely. Use encrypted file transfer, redact unrelated data, and log exactly what you provided.
Redaction: Removing sensitive or unrelated data from documents.
Secure Sharing: Using encryption or audit-safe platforms to send files.
Audit Trail: A record of what was shared and when.
Pre-Audit Essentials
With violations avoided and audit preparation complete, you’re positioned to face regulators with confidence and efficiency.
Download our Free HIPAA Compliance Template!
A ready-made HIPAA compliance template saves you hours of setup and gives you a clear starting point for audits.
Adjust tasks by role and organization size. For example, IT teams handle encryption while office staff focus on physical safeguards.
Download Free HIPAA Compliance Checklist (PDF + Sheet)
Once you’ve downloaded the template, you may still have specific questions. That’s where FAQs help.
FAQs
What exactly is included in a HIPAA compliance checklist?
A HIPAA compliance checklist in 2025 covers every requirement needed to protect protected health information (PHI) and electronic protected health information (ePHI). This includes HIPAA policies and procedures, staff training records with signed attestations, documented risk assessments and risk analyses, and Business Associate Agreements (BAAs) for all vendors and subcontractors handling patient data.
It also requires evidence of incident response procedures, breach notification workflows, and proof that you’ve implemented the required administrative safeguards, physical safeguards, and technical safeguards under the HIPAA Privacy Rule and the HIPAA Security Rule.
A strong HIPAA compliance requirements checklist also includes audit logs, access reviews, encryption evidence, and ongoing monitoring tasks to stay audit-ready year-round.
How often should I perform a HIPAA Risk Assessment vs Risk Analysis?
A HIPAA Risk Assessment should be performed at least once every year. This step identifies where your systems store medical records and patient data, maps data flows across EMR/EHR systems, and highlights risks to confidentiality, integrity, and availability.
A HIPAA Risk Analysis is more flexible and should be updated whenever you change systems, add a vendor, migrate to the cloud, or face new security threats.
Both are mandatory under the HIPAA Security Rule compliance checklist. Auditors expect to see evidence of a yearly risk assessment and documented updates to your risk analysis as systems and threats evolve.
What counts as a security incident vs a breach under HIPAA?
A security incident under HIPAA includes any unauthorized access attempt, suspicious login, or failed attempt to reach electronic protected health information (ePHI).
A HIPAA breach, by contrast, is when there is a confirmed disclosure of patient medical records or identifiable health information, whether by mistake or through malicious activity.
HIPAA requires covered entities and business associates to follow the Breach Notification Rule, which mandates notifying patients, the Department of Health and Human Services (HHS), and sometimes the media.
Both incidents and breaches must be logged with documentation and tracked as part of your HIPAA compliance audit checklist to prove compliance during investigations.
Are Business Associates directly liable under HIPAA?
Yes. Since the HIPAA Omnibus Rule, Business Associates and their subcontractors are directly responsible for HIPAA compliance. This includes IT service providers, cloud hosting vendors, billing firms, consultants, and legal services that handle PHI or ePHI on behalf of covered entities. Business Associates must sign Business Associate Agreements (BAAs) and implement the same technical safeguards, physical safeguards, and administrative safeguards as healthcare providers.
If they fail to protect patient data, they face the same civil and criminal penalties as covered entities under the HIPAA Enforcement Rule.
Is encryption required under the HIPAA Security Rule in 2025?
Yes. Starting in 2025, encryption is no longer optional or “addressable” under the HIPAA Security Rule. It is now mandatory.
This means you must encrypt all electronic protected health information (ePHI) at rest using AES-256 encryption and in transit using TLS 1.2 or higher.
This applies across systems, databases, mobile devices, cloud storage, and email. Encryption is a critical safeguard against unauthorized access and data breaches, and auditors will request proof of encryption settings during HIPAA compliance audits.
Without it, your organization risks significant fines under the updated HIPAA compliance requirements checklist.
What audit controls logs do I need to retain, and for how long?
You must maintain audit controls and system logs for a minimum of six years to satisfy HIPAA compliance audit requirements.
These logs must capture user identification, date and time of access, type of action performed, patient record accessed, and whether the attempt was successful or failed.
Retained logs include system activity logs, access control logs, and audit logs from EMR/EHR systems, servers, and applications.
Under the HIPAA Security Rule audit controls standard, these records provide evidence that you are monitoring, detecting, and responding to suspicious activity around protected health information (PHI).
How do I handle HIPAA compliance for software development teams?
For software development teams and SaaS vendors, HIPAA compliance must be built into the software development lifecycle (SDLC). This includes using secure coding practices, static and dynamic code scanning (SAST/DAST), dependency scanning, and formal change control procedures.
Cloud environments must enforce strong encryption of PHI, secrets management, detailed logging, and multi-tenant isolation if you serve multiple healthcare customers.
Any EMR/EHR integrations must include a Business Associate Agreement (BAA), data minimization policies, and detailed API access logging. Following a HIPAA compliance checklist for software development ensures your product is safe for handling electronic protected health information.
Do dental offices need a separate HIPAA compliance checklist?
Yes. Dental offices are considered covered entities under HIPAA and must follow the same rules as hospitals and clinics.
A HIPAA compliance checklist for dental offices includes securing front desk PHI exposure, placing workstations to block unauthorized viewing, shredding physical records, and wiping or reusing devices securely.
Dental practices must also implement email and fax security procedures, control verbal disclosures of patient information, and conduct annual staff training. Signed training attestations must be retained for six years.
These safeguards ensure compliance with both the HIPAA Privacy Rule and the HIPAA Security Rule.
What is the fastest way to get audit-ready with limited staff?
The fastest way to get HIPAA audit-ready is to use a HIPAA compliance software platform like ComplyJet. Automation tools let you map administrative, technical, and physical safeguards, assign tasks to owners, and centralize all compliance evidence in one secure location.
Instead of spending months compiling policies, training logs, Business Associate Agreements, and risk assessments, platforms like ComplyJet create audit-ready exports with one click.
Talk to Our Founders to Know More!
For small teams with limited resources, a HIPAA compliance software checklist can reduce preparation time from months to weeks.
Can HIPAA compliance software replace policy and training requirements?
No. HIPAA compliance software is a tool to automate evidence collection, task assignments, and audit readiness, but it cannot replace required written HIPAA policies or workforce training.
Every covered entity and business associate must still maintain HIPAA Privacy Rule and Security Rule policies, provide initial and ongoing staff training, and retain signed training records for six years.
HIPAA compliance software supports the process by reducing manual tracking and centralizing documentation, but policies and training remain mandatory under the HIPAA compliance requirements checklist.
Conclusion
HIPAA compliance in 2025 is not a one-time project. It’s a continuous program that needs monitoring, updates, and regular evidence reviews.
Enforcement is tougher, with higher penalties for missing safeguards, such as encryption or BAAs. The cost of inaction is far greater than the effort to comply.
Automation delivers real ROI by reducing manual effort, avoiding errors, and keeping your program ready for audits without draining your team.
Start your HIPAA program with ComplyJet: import the free template, map safeguards, assign owners, and track evidence automatically.
A Free Trial might help you understand how fast ComplyJet can get you HIPAA compliant!



