If you’re handling patient data in 2025, one question eventually surfaces: Who actually enforces HIPAA? Is it just one agency, or a patchwork of regulators waiting for you to slip? The answer isn’t simple.
HIPAA enforcement today is a shared responsibility, led by the U.S. Department of Health & Human Services’ (HHS) Office for Civil Rights (OCR), but supported by the Department of Justice (DOJ), CMS, state attorneys general, and even the FTC in specific cases. Add in your own Privacy and Security Officers, and you realize compliance is monitored both externally and internally.
This structure is what we call the HIPAA Enforcement Rule. Understanding it matters because penalties are real, with corrective action plans, and potential criminal charges. In 2025, the focus on security risk analysis, business associate oversight, and breach readiness has only intensified.
In this article, you’ll see exactly which agencies enforce HIPAA, how penalties are structured, where law enforcement fits in, and what you must do to stay compliant without wasting resources.
Let’s begin with the major question.
What is the HIPAA Enforcement Rule?
The HIPAA Enforcement Rule is the regulation that gives power to HIPAA. Codified at 45 CFR Part 160, it defines how violations are investigated, how penalties are applied, and how appeals work.
Originally published in 2006, the rule was shaped by criticism that HIPAA compliance seemed optional, since OCR resolved thousands of complaints without penalties.
The HITECH Act of 2009 changed that by reversing the burden of proof, extending compliance requirements to business associates, and requiring organizations to show evidence that a disclosure was not a breach.
The Final Omnibus Rule of 2013 then introduced a four-tier penalty system, scaling fines based on culpability. This moved HIPAA away from a “voluntary compliance” era toward a structure where real consequences are tied to negligence or willful neglect.
Today, the Enforcement Rule guides regulators in every HIPAA case, from a patient complaint to systemic failures or criminal misuse of PHI referred to the Department of Justice.
What Does the HIPAA Enforcement Rule Cover?
The Enforcement Rule applies to the Privacy Rule, Security Rule, Breach Notification Rule, and Administrative Simplification provisions. Each focuses on a different aspect of protecting patient data and healthcare transactions.
- Privacy Rule: Defines when PHI can be used or disclosed, and ensures patients can access and amend their records.
- Security Rule: Requires administrative, physical, and technical safeguards to protect ePHI, from access controls to risk analyses.
- Breach Notification Rule: Mandates prompt disclosure to affected individuals, HHS, and sometimes the media when PHI is compromised.
- Administrative Simplification: Standardizes electronic transactions, identifiers, and code sets to streamline healthcare operations.
Enforcement can begin with small issues like a patient complaint about a nurse’s unauthorized access, or large failures such as systemic billing errors.
OCR alone has reviewed over 300,000 complaints since 2003, with most resolved through technical assistance or corrective action rather than fines.
By covering every major HIPAA rule, the Enforcement Rule creates a single enforcement backbone that regulators and organizations alike must follow.
How Do Penalties Work Under the Enforcement Rule?
The HIPAA Enforcement Rule established a tiered penalty system that scales based on how negligent the organization was. These tiers are updated annually for inflation, and in 2025 the maximum annual cap exceeds $2 million per violation type.
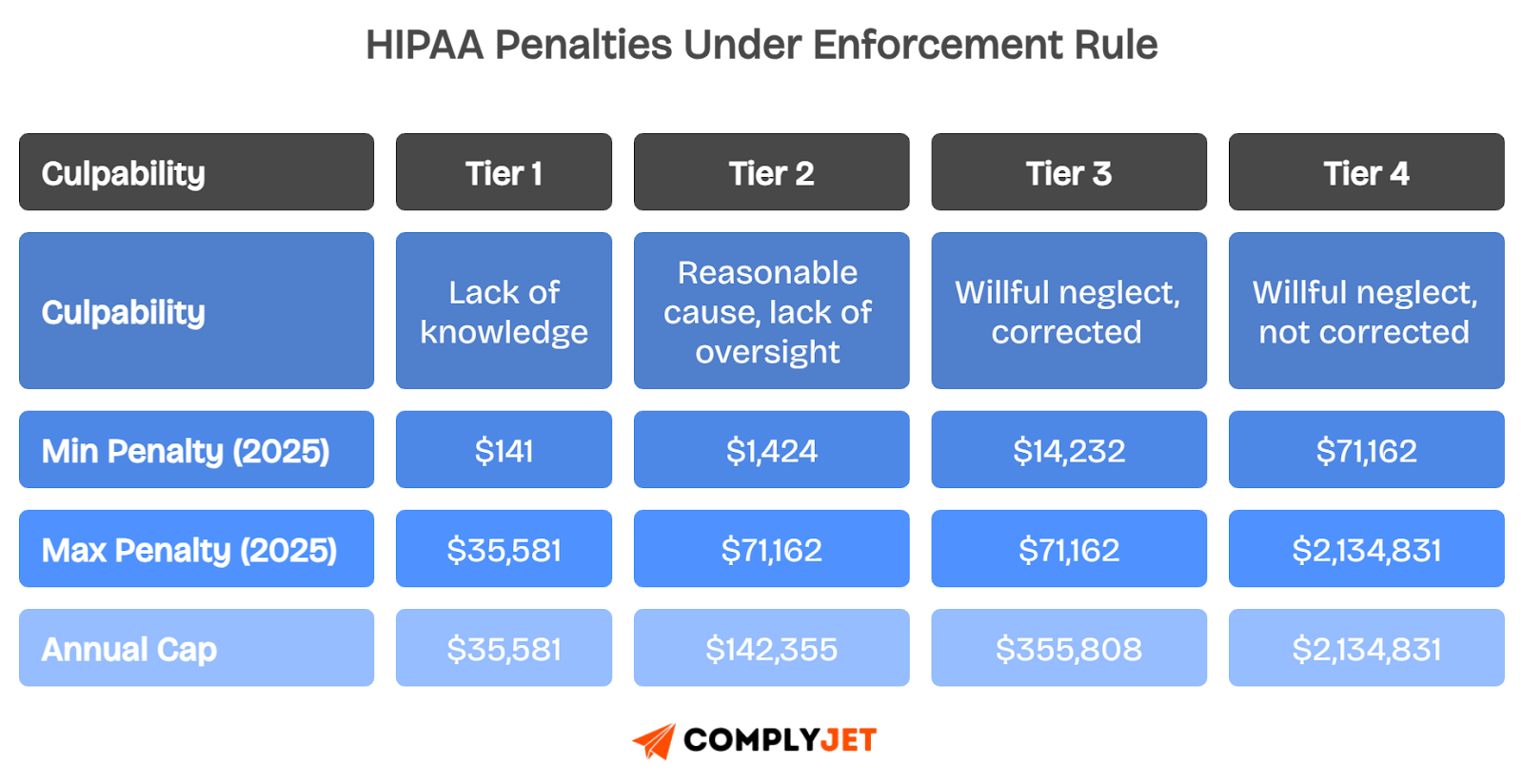
Fines are only one part of the picture. Regulators may also require Corrective Action Plans (CAPs), which force organizations to retrain staff, rewrite policies, or overhaul technical safeguards. These indirect costs can easily exceed the fines themselves.
Civil penalties aside, when misuse of PHI is deliberate, such as selling medical records or accessing data for personal gain, the case escalates to the DOJ for criminal prosecution, where prison time is possible.
Who enforces HIPAA at the federal level today?
To understand HIPAA enforcement in practice, you need to know which agencies share responsibility and how each agency handles investigations, penalties, and compliance oversight. Enforcement is not centralized under one office. Instead, multiple federal and state agencies have defined roles, and inside your own organization, appointed officers carry daily responsibility.
Agency Enforcement Overview
1. The Office for Civil Rights (OCR) - Primary Enforcer
If you ask who enforces HIPAA, the answer starts with the Department of Health and Human Services’ Office for Civil Rights. OCR is the frontline agency for HIPAA compliance.
OCR investigates complaints submitted by patients or whistleblowers, runs random and targeted compliance audits, and enforces the Privacy, Security, and Breach Notification Rules.
Their toolbox includes voluntary resolution agreements, corrective action plans, civil monetary penalties, and referrals to the Department of Justice when criminal intent is suspected. Penalties follow a tiered structure that scales from “lack of knowledge” violations to “willful neglect” left uncorrected.
OCR also provides technical assistance, so many cases resolve without penalties. Still, fines can exceed two million dollars annually for severe violations.
2. Centers for Medicare & Medicaid Services (CMS)
CMS enforces the Administrative Simplification provisions. These include healthcare transaction standards, code sets, and unique identifiers like NPIs. Their work ensures interoperability and consistency in claims, billing, and eligibility checks.
Complaints about transaction standards flow through the Administrative Simplification Enforcement Testing Tool (ASETT), which CMS uses to track noncompliance.
CMS enforcement typically begins with technical guidance. For persistent violations, CMS can impose corrective actions or even restrict participation in federal programs. This makes CMS a key player in keeping the “plumbing” of healthcare standardized and secure.
3. Department of Justice (DOJ)
The DOJ enforces criminal HIPAA violations. These are cases where there is willful misuse of protected health information (PHI), often for financial gain or malicious harm.
Examples include selling patient records, identity theft schemes, or intentional disclosures of PHI without authorization.
Penalties are serious: fines can reach $250,000 per offense, and prison sentences can extend up to 10 years, depending on the level of intent.
OCR refers criminal cases to the DOJ under 42 U.S.C. § 1320d-6, ensuring that civil enforcement escalates to criminal prosecution when necessary.
4. State Attorneys General
Since the HITECH Act of 2009, State Attorneys General (AGs) gained the power to enforce HIPAA at the state level. This expansion of authority was later reinforced by the Omnibus Rule of 2013.
State AGs can bring civil actions in federal court on behalf of residents affected by HIPAA violations. Penalties are smaller than OCR fines, often capped at $25,000 per year per violation type, but they provide an additional enforcement pathway.
This gives states a role alongside federal agencies, increasing accountability for local healthcare organizations and business associates.
5. Federal Trade Commission (FTC)
The FTC fills HIPAA’s enforcement gaps. It oversees entities not traditionally bound by HIPAA, such as mobile health apps, fitness trackers, and personal health record (PHR) vendors.
The FTC uses its Section 5 powers to regulate unfair or deceptive practices, particularly when companies fail to notify consumers of data breaches or misuse personal health information.
This ensures that consumer health privacy is protected even outside HIPAA’s traditional scope.
Now, let’s see what brings forth an enforcement action.
What Are the Enforcement Triggers and Likely Outcomes?
The Enforcement Rule gives regulators a flexible set of tools, designed to match penalties to the seriousness of the violation. Here’s how enforcement typically progresses:
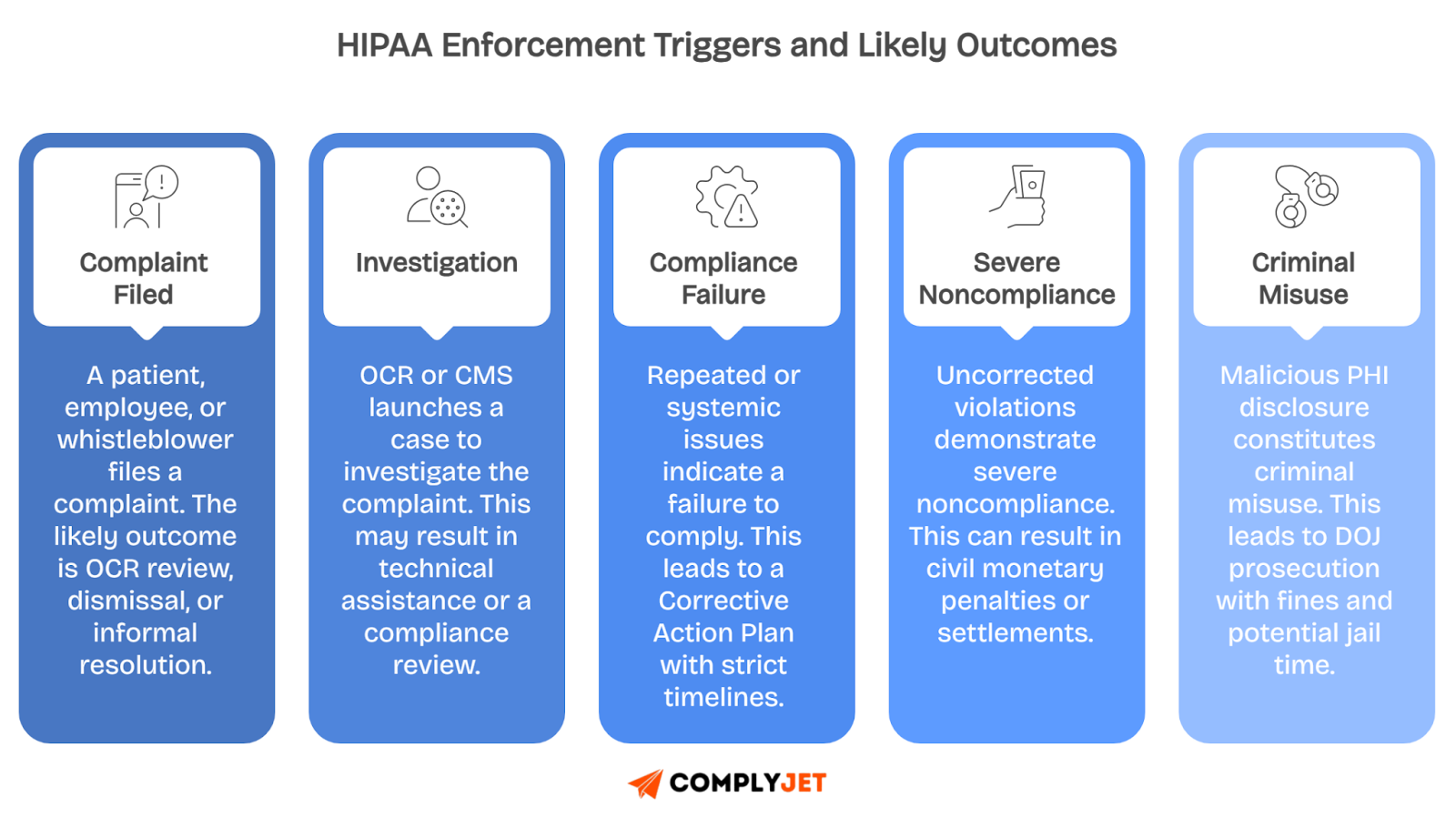
When issues are minor, regulators often start with technical assistance, essentially coaching entities on fixes. Larger problems lead to Corrective Action Plans (CAPs) that are mandatory programs that require retraining staff, updating policies, and performing new risk assessments.
If an organization fails to cooperate or shows willful neglect, agencies can impose resolution agreements, monetary settlements, or civil penalties.
At the highest level, intentional misuse of patient data triggers DOJ criminal referrals, where penalties can include fines up to $250,000 and imprisonment up to 10 years.
This tiered system gives regulators flexibility while ensuring accountability. It shows why HIPAA enforcement touches everything from IT safeguards to front-desk privacy practices.
Now that you know the basics of how the HIPAA Enforcement Rule works, the next step is understanding who actually enforces HIPAA in practice.
Who Enforces the HIPAA Privacy Rule and Breach Notification Rule?
The HIPAA Privacy Rule and the HIPAA Breach Notification Rule are enforced primarily by the Office for Civil Rights (OCR) at the Department of Health and Human Services.
OCR is responsible for making sure covered entities and business associates protect patient data, honor patient rights, and properly report data breaches when they occur.
When a privacy complaint is filed, such as a patient alleging unauthorized access to their records, OCR determines whether the claim falls within HIPAA’s scope. If it does, OCR can open an investigation, request documentation, and review how policies and safeguards are implemented in practice.
For the Breach Notification Rule, OCR requires healthcare organizations and business associates to notify affected patients, the Secretary of HHS, and sometimes the media, when unsecured PHI is compromised. Failure to send proper notices or delays in reporting can trigger enforcement.
Enforcement starts with technical assistance when issues appear minor or unintentional. For systemic failures, OCR can impose corrective action plans, force retraining, or require risk assessments. When organizations fail to comply or ignore remediation, OCR escalates to civil monetary penalties, with fines that can exceed $2 million annually per violation category.
Both rules are also linked to criminal referrals. If a privacy violation shows intent to profit or cause harm, OCR refers the case to the Department of Justice (DOJ) for prosecution.
Together, these rules are the backbone of patient trust, and OCR’s enforcement ensures organizations cannot ignore their duty to keep health information safe.
Who is responsible for enforcing the HIPAA Security Rule?
The HIPAA Security Rule focuses on protecting electronic patient information, and the Office for Civil Rights (OCR) at HHS is responsible for enforcing it federally.
OCR enforces by reviewing risk analyses, technical safeguards, and documented compliance measures, making sure covered entities and business associates protect patient information properly.
Inside your organization, you must designate a Security Officer responsible for policies, risk assessments, access management, and incident response planning to satisfy HIPAA requirements.
By combining OCR oversight with internal governance, enforcement of the HIPAA Security Rule becomes both a federal mandate and an operational responsibility for every entity.
Security Rule readiness in 7 steps
- Conduct a thorough security risk analysis each year
- Implement administrative safeguards such as training and policies
- Apply physical safeguards for device and facility security
- Deploy technical safeguards like access controls and encryption
- Monitor system activity with audit logs and alerts
- Establish an incident response plan with defined roles
- Document all compliance actions for evidence in audits
A complete approach ensures compliance with the HIPAA Security Rule, and next you should understand which other agencies enforce HIPAA beyond OCR.
Which governing agencies enforce HIPAA beyond OCR?
While OCR leads federal enforcement, other governing agencies also enforce HIPAA regulations, creating additional accountability pathways for covered entities and their associates.
State Attorneys General have the authority to bring civil actions on behalf of residents, especially after the HITECH Act and Omnibus Rule extended their enforcement powers.
The Omnibus Rule explicitly gave enforcement authority to State Attorneys General, enabling them to pursue HIPAA violations independently and seek damages in federal court.
The Federal Trade Commission (FTC) regulates non-covered entities, including personal health record vendors, ensuring breach notifications and addressing unfair practices under Section 5 powers.
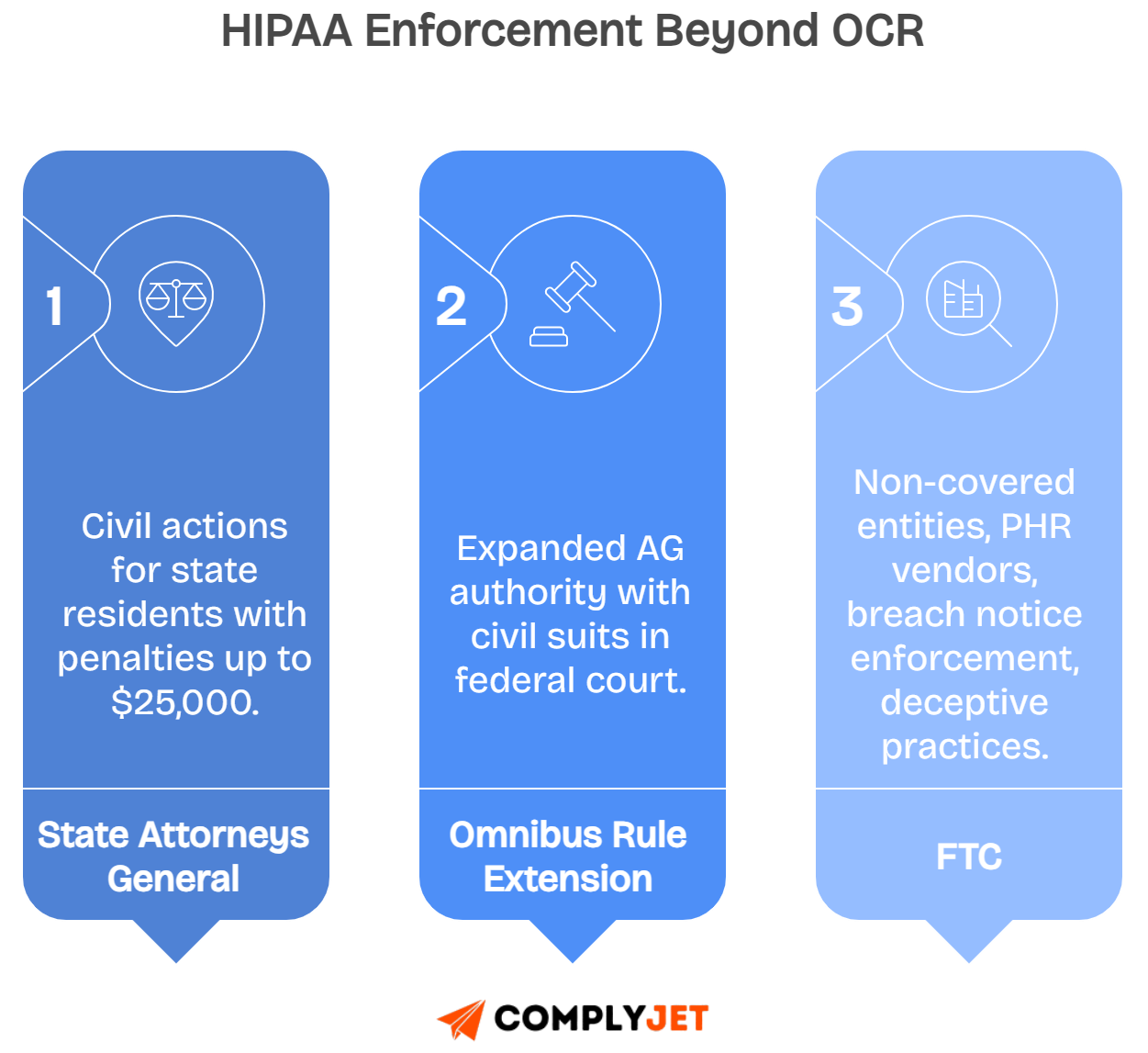
These overlapping responsibilities ensure HIPAA enforcement works across both federal and state levels, transitioning into how coordination between agencies maintains compliance consistency.
Does HIPAA apply to law enforcement, and what are the exceptions?
HIPAA regulations apply to covered entities and business associates, not directly to law enforcement agencies or officers requesting protected health information.
Healthcare providers remain responsible for ensuring HIPAA compliance when responding to police requests, which means disclosures must follow specific exceptions outlined in the Privacy Rule.
Understanding these exceptions helps you avoid violations while still cooperating with legitimate law enforcement investigations that require access to health information.
By applying the right safeguards, you reduce risk while ensuring HIPAA rules are respected during law enforcement interactions.
Law enforcement exceptions that allow disclosure
Disclosures without patient authorization are allowed when valid legal authority or urgent circumstances exist under HIPAA’s Privacy Rule.
Court orders and subpoenas require you to release information, while administrative requests often apply in fraud or healthcare program investigations.
Emergencies and safety threats allow disclosure if public security is at immediate risk, while identification exceptions apply for suspects, victims, or decedents.
Reporting crimes committed on healthcare premises is also permitted, provided you follow the minimum necessary disclosure requirement.
Law Enforcement Exceptions Under HIPAA
Each exception comes with boundaries, requiring careful documentation and limiting disclosure only to what is truly necessary.
Minimum necessary and documentation reminders
Always disclose the minimum information needed, such as identifiers instead of full records, when responding to law enforcement under HIPAA.
Record the legal request, scope of information shared, and your justification for disclosure in compliance logs to prove compliance if later questioned.
Training your team to document these steps ensures consistency, reduces liability, and protects patient privacy during law enforcement requests.
These documentation habits demonstrate due diligence and prepare you for audits or OCR reviews.
Can law enforcement violate HIPAA? No, only covered entities can, but officers may improperly request PHI beyond the allowed scope.
Does HIPAA block reporting a crime? No, HIPAA allows reporting crimes, especially if committed on premises or during emergencies.
What to record when disclosing PHI to police? Always note request type, scope of disclosure, and reason for release in your compliance logs.
Clear documentation of law enforcement disclosures helps you prove compliance, which ties directly into understanding internal responsibilities for HIPAA enforcement.
Who is responsible for HIPAA enforcement inside an organization?
HIPAA enforcement is not only about federal oversight; it also requires clear accountability inside your organization with specific officers managing compliance.
You must appoint a Privacy Officer responsible for policies, patient rights requests, and ensuring privacy practices are consistently followed across the workforce.
You must also designate a Security Officer who develops technical safeguards, conducts security risk assessments, and manages access controls for electronic protected health information.
In larger organizations, consider an optional Compliance Officer who oversees the entire HIPAA program, coordinates training, and ensures risks are addressed across departments.
Governance rhythm for internal enforcement
- Conduct annual or bi-annual risk analyses and document identified vulnerabilities
- Update policies regularly to match current regulations and operational changes
- Deliver recurring training programs to staff, adjusted for role-specific risks
- Review vendor agreements and verify business associate compliance annually
- Test incident response drills to ensure breach readiness and reporting timelines
RACI chart for HIPAA enforcement responsibilities
Establishing these roles and rhythms ensures your compliance structure is solid, which connects directly into how external complaints are filed and resolved.
How are complaints filed, and what happens after?
Complaints about HIPAA violations can be filed by patients or individuals directly through government portals or enforcement agency websites.
Patients submit complaints through the OCR portal for privacy and security concerns, CMS ASETT for administrative simplification issues, or State AG sites for civil actions.
For entities outside the HIPAA scope, such as health record vendors, complaints go to the FTC, which investigates deceptive or unfair health data practices.
Once filed, investigators review evidence such as risk assessments, staff training records, compliance policies, vendor contracts, and audit trails to evaluate violations.
Possible outcomes after complaint investigations
- Technical assistance is offered for minor or first-time violations
- Corrective Action Plans (CAPs) require documented remediation steps
- Monetary settlements or civil penalties are imposed for serious issues
- Criminal referrals are made to the DOJ for intentional or malicious acts
Understanding this complaint process helps you prepare documentation in advance, which supports proactive compliance and reduces enforcement risks in your organization.
What HIPAA enforcement rule trends matter in 2025?
HIPAA enforcement in 2025 focuses heavily on technical maturity, with agencies expecting stronger documentation and better safeguards than in prior years.
The Security Rule is under greater scrutiny, and you are expected to implement multi-factor authentication, complete thorough risk analyses, and demonstrate consistent security practices.
Reproductive health privacy requires signed attestations before disclosures, limiting when and how sensitive information can be shared with third parties or law enforcement.
Penalties are inflation-adjusted, and OCR continues announcing settlements, making proactive documentation and automated compliance monitoring essential for reducing enforcement risks.
Key Enforcement Trends in 2025
See where you stand in minutes.
Book a ComplyJet demo to check your HIPAA readiness before issues turn into penalties.
These enforcement patterns make it clear that your next step is building internal practices that prevent violations before they reach regulators.
What should you do now to avoid enforcement action?
Avoiding HIPAA enforcement requires consistent internal action, with every step documented, tested, and available for review during audits or investigations.
First, complete and document a Security Risk Analysis, identifying vulnerabilities, and record remediation steps taken to address high-risk areas immediately.
Next, update privacy and security policies regularly, provide role-based training for staff, and retain evidence of attendance and training completion.
Also, review Business Associate Agreements and vendor security practices annually, testing your incident response and breach notification procedures each year.
Finally, monitor access controls, apply MFA across systems, and retain audit logs to provide regulators with verifiable evidence of ongoing HIPAA compliance.
Action Checklist to Avoid Enforcement
By executing this checklist, you reduce enforcement risks and prepare your organization for any level of HIPAA review or investigation.
How ComplyJet helps you satisfy the HIPAA Enforcement Rule quickly
ComplyJet helps you meet HIPAA enforcement requirements by automating evidence collection, mapping safeguards, generating policy kits, and maintaining audit trails with direct founder-led support.
With our tools, you streamline repetitive compliance work while keeping every control mapped and every policy up to date for audits.
This approach saves time for lean teams and shortens the path to audit-readiness without requiring additional compliance staff or outside consultants.
ComplyJet HIPAA Enforcement Features
Most customers get audit-ready within weeks, even with small teams, showing how automation reduces both effort and cost.
See how ComplyJet does it faster and at a lower cost, and the exact workflows we automate.
Start our FREE TRIAL!
FAQs
Who enforces HIPAA regulations?
The Office for Civil Rights (OCR) at HHS is the primary enforcer, supported by CMS, DOJ, State Attorneys General, and the FTC in specific areas.
How often does OCR actually fine organizations under HIPAA?
Most complaints end in technical assistance or corrective action, not fines. But when systemic failures or willful neglect are proven, OCR issues penalties that can exceed $2 million annually.
Does HIPAA enforcement differ for small practices compared to large hospitals?
The rules are the same, but OCR considers size, resources, and compliance efforts. Small practices often get guidance or CAPs, while larger entities face higher penalties.
Can HIPAA violations lead to personal liability for executives?
Yes. If executives knowingly allow violations or fail to correct willful neglect, OCR and DOJ can hold them accountable. Penalties include personal fines and, rarely, jail time.
How does OCR decide between technical assistance and penalties?
They look at intent, impact, and remediation. If you fix the issue quickly and show effort, OCR favors technical guidance. Ignoring risks or repeat offenses leads to penalties.
What happens if a Business Associate violates HIPAA?
Since the HITECH Act, Business Associates are directly liable. OCR can investigate them, impose CAPs, or issue penalties just like covered entities. No longer can they shift blame upstream.
Are HIPAA audits still happening in 2025?
Yes, but selectively. OCR paused broad audits during COVID, then restarted with targeted reviews in 2023. In 2025, audits focus heavily on Security Rule safeguards and breach readiness.
How quickly must you notify patients under the Breach Notification Rule?
You must notify without unreasonable delay, and no later than 60 days after discovery. Regulators expect proof of when you discovered the breach and your notification timeline.
Can state laws impose stricter enforcement than HIPAA?
Yes. HIPAA sets a federal baseline, but states can create stricter privacy rules. State Attorneys General enforce both HIPAA and state laws, often bringing civil actions in federal court.
Does HIPAA enforcement apply to telehealth apps and platforms?
If the app handles PHI as a covered entity or Business Associate, HIPAA applies. If not, the FTC enforces privacy through breach notification and unfair practice laws. Many telehealth vendors fall under both.
What’s the most common mistake organizations make during an OCR investigation?
Not having documentation ready. Regulators want to see risk analyses, policies, training logs, and vendor contracts. Saying “we did it” without proof is treated as non-compliance.
Conclusion
You now understand who enforces HIPAA and how the HIPAA Enforcement Rule operates across federal, state, and organizational levels in 2025.
The clear next step is preparing your risk analysis, updating documentation, and automating evidence collection to stay ahead of audits and investigations.
ComplyJet makes this simpler by giving you audit-ready tools designed for small teams, helping you protect patient information while avoiding costly penalties.
Talk to Our Founders Now!



